Cyber Security vs Network Security: What You Need to Know
Keeping your data safe in 2026 takes more than just a firewall; it requires an ecosystem of network security solutions. This guide explores how AI, zero-trust, and tools like Kuikwit are helping businesses stay secure and responsive in a high-threat digital world.

Protecting your digital assets with robust network security solutions is no longer a luxury; it’s a non-negotiable part of staying in business in a world where a single breach can sink a company overnight. It’s about building a multi-layered defense that guards your data, your employees, and your reputation from increasingly sophisticated threats that don't take a day off. Whether you’re a small shop or a massive enterprise, the goal is the same: keep the bad actors out and the good data flowing without any hiccups.
What is a Network Security Solution?
It's a combination of hardware, software, and policies designed to protect the integrity, confidentiality, and accessibility of a computer network and its data. Think of it as a digital shield that monitors everything coming in and out, blocking the garbage while letting the essential traffic through.
Is professional network security worth the cost?
Absolutely, because the cost of a data breach—fines, lost trust, and downtime—is almost always exponentially higher than the monthly fee for a solid defense. It’s like insurance for your digital life; you hope you never need the "heavy" stuff, but you’ll be glad it’s there when a hacker starts knocking.
How does it actually work?
It works in layers—starting with firewalls to block the perimeter, then moving to intrusion detection systems that watch for sneaky behavior inside, and finally using encryption to make sure that even if data is stolen, it's unreadable. In modern environments, especially where businesses rely heavily on digital customer support systems, this layered protection becomes even more critical. It’s a constant, 24/7 cycle of monitoring, updating, and reacting to new threats as they emerge.
The shifting landscape of network security solutions in 2026

The way we approach network security solutions has changed so much just in the last year. It used to be that you could just "set it and forget it" with a basic firewall, but the 2026 threat landscape is way too aggressive for that. Now, everything is about agentic AI and automated defense. Hackers are using bots to find tiny cracks in your code at 3 AM, so you need a system that can fight back without waiting for a human to wake up. It’s a bit of an arms race, honestly. If you aren't using tools that can learn and adapt on the fly, you're basically bringing a knife to a laser-gun fight.
Why a cyber intelligence centre is the brain of your defense
Having a cyber intelligence centre is like having a private detective agency that never sleeps. They don't just wait for an alarm to go off; they’re out there on the dark web, looking for chatter about new vulnerabilities before they ever hit your network. This proactive approach is what separates the "survivors" from the "victims." When you have that level of deep insight powered by advanced AI-driven threat intelligence, you can patch a hole before the rain even starts. It’s about moving from a reactive "hope for the best" strategy to a proactive "know what's coming" stance that gives you a massive competitive edge.
Navigating cyber security solutions for small business
Most small shop owners think they're "too small to be a target," but that's exactly what makes them low-hanging fruit. Real-world cyber security solutions for SMBs need to be simple but effective. You don't need a million-dollar command center, but you do need basics like managed firewalls and automated backups. It’s about protecting your cash flow and your customer list. If a local bakery gets hit with ransomware, it's not just a technical problem; it’s a "we can’t pay our staff this week" problem. Keeping it simple but robust is the key to staying alive in a digital economy.
Why every it support company is now a security company
If your it support company isn't talking to you about security every single month, they aren't doing their job. In the old days, they were just the people you called when the printer was acting up. Now, they have to be your primary line of defense. They’re the ones managing your information security policies and making sure your staff isn't clicking on sketchy links. It’s a total shift in responsibility. You need a partner who understands that uptime is irrelevant if the data being served is compromised. They should be looking at your network not just as a set of wires, but as a vault.
The technical reality of cisco jobs in 2026
When you look at the current market, cisco jobs are no longer just about plugging in routers. They’re about architecting complex, self-healing networks that can isolate a threat in milliseconds. The demand for people who can handle IT security at a high level is through the roof. It’s not just about knowing the hardware; it’s about understanding the logic of a zero-trust environment. You need professionals who can build a network where every single device is treated like a potential intruder until proven otherwise. It’s a paranoid way to build a system, but it’s the only way to stay safe right now.
Comparing it security vs information security
A lot of people use these terms interchangeably, but there's a slight difference that matters for your strategy. It security is mostly about the "stuff"—the servers, the wires, and the devices. Meanwhile, information security is about the "data" itself, regardless of where it lives. You could have a super-secure server, but if your employees are texting client credit card numbers over unencrypted apps, your info security is zero. A good it service provider will look at both. They'll secure the pipes, but they'll also help you set policies so the "water" inside doesn't get contaminated.
| Component | Primary Function | Why it matters in 2026 |
| Next-Gen Firewall | Traffic filtering | Blocks AI-driven bot attacks |
| Zero-Trust Access | Identity verification | Stops stolen credentials from working |
| Managed XDR | Unified monitoring | Connects the dots between different attacks |
| End-to-End Encryption | Data scrambling | Makes stolen data useless to hackers |
Why it support companies are pushing managed detection
You'll notice that almost all it support companies are now offering MDR (Managed Detection and Response). This is because traditional antivirus is pretty much dead against modern malware. You need "eyes on glass" 24/7. This doesn't mean a guy is staring at a screen for 8 hours; it means an AI is staring at it, and it pings a human expert the second something looks "weird." It’s that human-plus-machine combo that makes network security and general defense so powerful. It gives you the scale of a robot with the intuition of a seasoned veteran who has seen every trick in the book.
Setting up your network solutions login for safety

It sounds boring, but the way you handle your network solutions login is actually one of your biggest vulnerabilities. Most breaches don't happen through some genius code exploit; they happen because someone used "Password123" and didn't have MFA turned on. A solid it services company will enforce strict credential policies. They’ll move you toward passwordless logins or biometric auth because passwords are the weakest link in the chain. If your login process feels "too easy," it probably is, and that’s a red flag you shouldn't ignore.
Why business security solutions must include employee training
You can have the most expensive business security solutions in the world, but if your receptionist clicks on a "FedEx Delivery Failed" link, the hackers are in. Human error is still the cause of nearly 95% of breaches. That’s why training is a core part of any network support plan. You have to teach people how to spot a deepfake voice or a sophisticated phishing email. It’s about building a "human firewall." When your team knows what to look for, they become your most active defenders instead of your biggest liability.
Scaling with a global it services provider
If you're operating in multiple countries, you need an it services provider that can handle different time zones and different legal requirements. Network security services in the EU look different than they do in Australia due to things like GDPR. A global partner ensures that your business security is consistent across every branch. They can manage your network security from a central hub while providing local support when a physical cable gets snagged. It’s about having a unified posture so that a weakness in a small branch office doesn’t bring down the entire global corporation.
Streamlining support with Kuikwit.com
In the middle of all this high-tech defense, you still have to actually talk to your customers. This is where Kuikwit.com is a total life-saver for modern teams. It’s a customer support platform that pulls all your messages from WhatsApp, Facebook, Instagram, and more into one single, easy-to-use dashboard.
Think about the security risk of having ten different employees logged into five different social media accounts on their personal phones. Kuikwit centralizes everything, which is way more secure. It lets teams respond faster with features like chat assignment and AI-powered auto-replies, and it gives you analytics so you can actually see what’s happening. It turns a messy, multi-channel headache into a streamlined, secure conversation hub.
Common mistakes in network security implementation
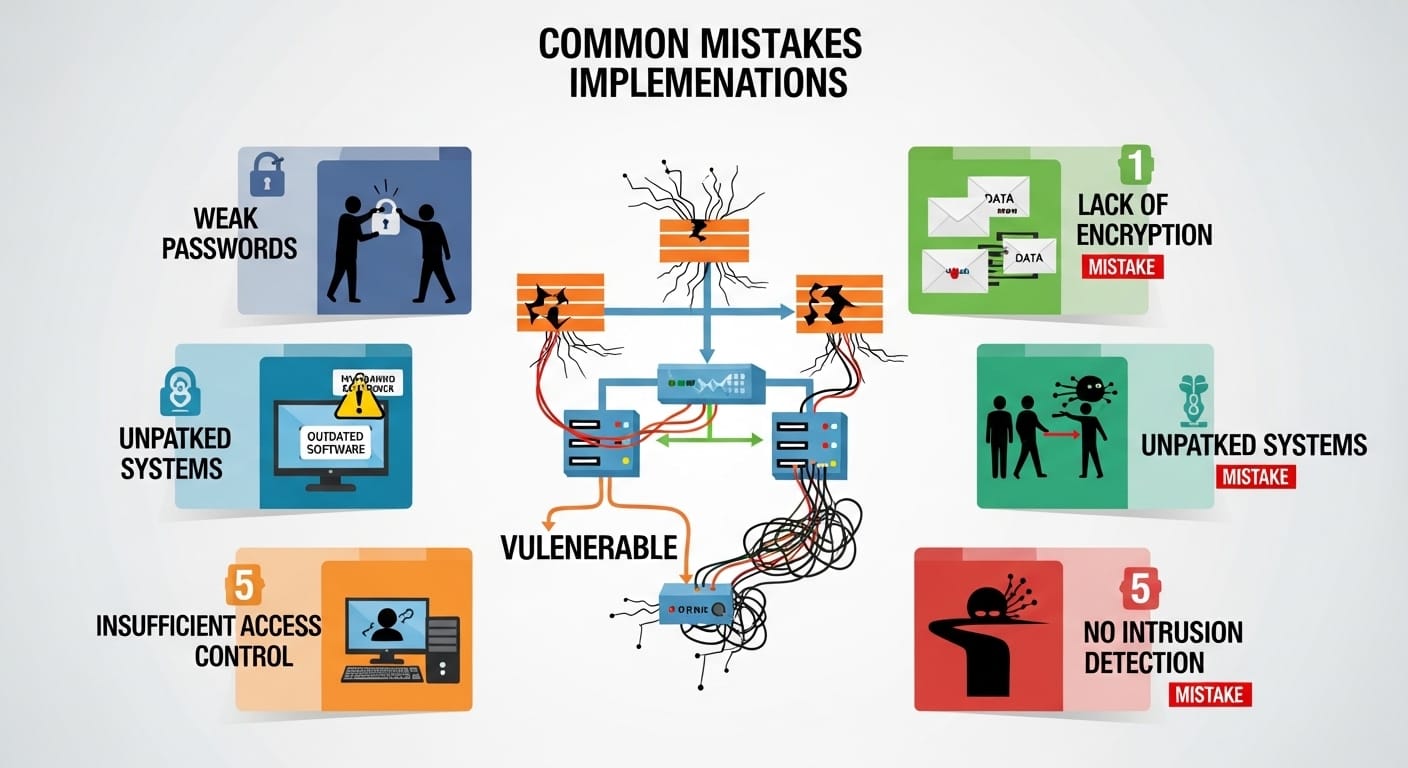
The biggest mistake? Thinking you're "done" once you install the software. Network security is a journey, not a destination. Another huge slip-up is failing to segment your network. If your guest Wi-Fi isn't separated from your main server, you're asking for trouble. Also, a lot of companies ignore their "shadow IT"—those random apps that employees download without asking. If it’s on your network and you aren't managing it, it’s a potential backdoor. You have to have total visibility into every single thing that touches your wires, or you're just guessing.
The future of network security services
Looking ahead, we're seeing a massive move toward "Secure Access Service Edge" (SASE). It’s a fancy way of saying that security is moving to the cloud because that's where the workers are. With so much remote work, the old "castle and moat" model doesn't work anymore because half the people aren't in the castle. Security solutions are becoming more identity-centric. It doesn't matter where you are; what matters is who you are and what device you're using. It’s a more flexible, more powerful way to protect a modern, mobile workforce.
FAQ: What People Also Ask About Network Security
1. Is there a difference between network security and cyber security?
Yeah, a bit. Think of network security as the locks on the doors and the guards in the hall. Cyber security is the broader field that also covers things like cloud safety, application code, and even the physical security of the server room.
2. How often should we do a security audit?
Ideally? At least once a year, or whenever you make a big change to your setup. A professional it consulting company can run a "penetration test" where they basically try to hack you (with permission) to find the holes before the real bad guys do.
3. Do small businesses really need a cyber intelligence centre?
Not your own private one, but you should definitely work with an it service provider that subscribes to one. It gives you the benefit of that high-level data without the "enterprise" price tag.
4. What is "Zero Trust"?
It’s a philosophy that says "trust no one, verify everyone." Even if you’re logged into the office Wi-Fi, the system still checks your identity before letting you into the sensitive files. It prevents one hacked account from ruining the whole company.
5. How does Kuikwit keep my customer data safe?
By centralizing all your DMs into one platform, you don't have sensitive customer info floating around on a dozen different personal devices. It’s a controlled, audited environment that keeps your business and your customers a lot safer.
Anyway, that’s the long and short of it. The digital world is getting crazier every day, but with the right layers of defense and a solid partner in your corner, you can stay ahead of the mess. Just remember to keep your software updated and don't trust any "urgent" emails from the CEO asking for gift cards. Catch you on the next one...